C 5 9 F 32
gasmanvison
Sep 23, 2025 · 5 min read
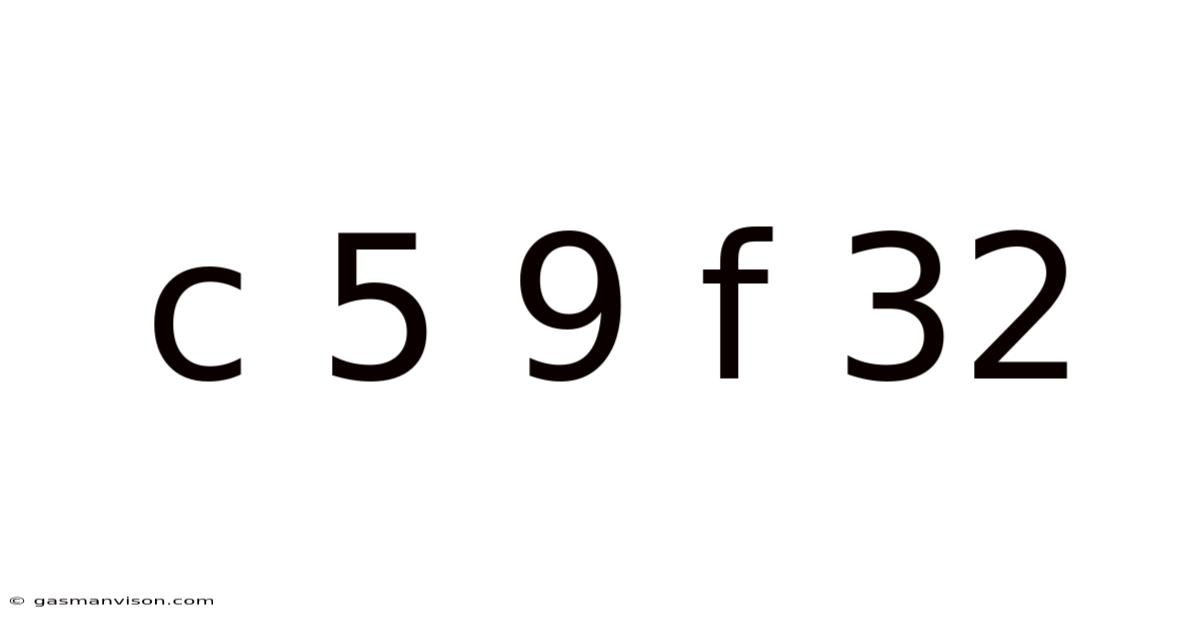
Table of Contents
Decoding the Enigma: A Deep Dive into "C 5 9 F 32" and its Cryptographic Implications
This seemingly random string of characters, "C 5 9 F 32," holds a fascinating potential for exploration, particularly within the context of cryptography and data security. While it doesn't inherently represent a known, established cipher or code, its very ambiguity opens the door to a discussion of various cryptographic principles and techniques. This article will delve into the potential interpretations of this sequence, exploring various cipher types and the broader landscape of data encryption. We'll also examine the importance of key length and complexity in securing sensitive information.
Understanding the Basics of Cryptography
Before we attempt to decipher "C 5 9 F 32," let's establish a fundamental understanding of cryptography. Cryptography, at its core, is the practice and study of techniques for secure communication in the presence of adversarial behavior. It encompasses two main branches:
-
Symmetric-key cryptography: This involves using the same key for both encryption and decryption. Examples include AES (Advanced Encryption Standard) and DES (Data Encryption Standard). The security of these methods hinges heavily on the secrecy and strength of the key.
-
Asymmetric-key cryptography (Public-key cryptography): This utilizes two separate keys: a public key for encryption and a private key for decryption. RSA (Rivest-Shamir-Adleman) is a prominent example. This allows for secure communication even without pre-shared secrets.
Possible Interpretations of "C 5 9 F 32"
Given the mixture of hexadecimal characters (C, F) and decimal numbers (5, 9, 32), "C 5 9 F 32" could represent several things, none of which are definitive without further context. Let's explore some possibilities:
1. Hexadecimal Representation:
The presence of "C" and "F" suggests a possible hexadecimal encoding. Hexadecimal is a base-16 number system frequently used in computing to represent binary data in a more compact form. However, without knowing the intended encoding scheme (e.g., ASCII, UTF-8), interpreting this sequence directly is impossible. For example, "C" in hexadecimal is 12 in decimal, and "F" is 15. However, simply converting each character independently doesn't yield a coherent message. We would need additional information about the encoding method and potential padding to make sense of this possibility.
2. Part of a Larger Ciphertext:
It's highly probable that "C 5 9 F 32" is merely a fragment of a larger ciphertext. A single, short sequence like this is unlikely to represent a complete message, especially when using sophisticated encryption algorithms. Modern encryption typically uses much longer keys and results in significantly longer ciphertext. The true meaning would only be revealed upon uncovering the entire encrypted message and identifying the used cipher.
3. A Key Fragment or Initialization Vector (IV):
This string might represent a segment of a cryptographic key or an initialization vector (IV). An IV is a random number used in conjunction with a cryptographic key to provide additional security and prevent the same plaintext from being encrypted to the same ciphertext. This is especially relevant in block ciphers like AES, where the same key and plaintext could yield the same ciphertext, making cryptanalysis easier. In this case, "C 5 9 F 32" might be part of a longer key or IV necessary for decryption.
4. A Custom Cipher or Code:
There's always the possibility that "C 5 9 F 32" is a part of a custom-designed cipher or code, specifically created for a particular application or purpose. Custom ciphers, while potentially offering unique security features, often require detailed knowledge of their design and implementation for successful decryption. Breaking a custom cipher without this knowledge can be incredibly challenging, and often requires advanced cryptanalytic techniques.
The Importance of Key Length and Complexity
Regardless of the interpretation of "C 5 9 F 32," the underlying principles of cryptographic security remain paramount. The strength of any encryption system relies heavily on the length and complexity of the key used. Shorter keys are significantly more vulnerable to brute-force attacks – attempts to guess the key by trying all possible combinations.
Modern cryptography advocates for using keys of sufficient length to resist even the most powerful computational resources. For symmetric encryption, key sizes of 128 bits or more are generally considered secure. Asymmetric encryption keys typically require even larger key sizes.
Advanced Cryptographic Techniques
Beyond basic symmetric and asymmetric encryption, a variety of other cryptographic techniques enhance security:
-
Hashing: This process transforms data of arbitrary size into a fixed-size string (a hash). Hashing is used for data integrity checks and password storage. Secure hashing algorithms produce unique hashes, even for minor changes in input data. SHA-256 and SHA-3 are examples of widely used secure hashing algorithms.
-
Digital Signatures: These provide authentication and non-repudiation. A digital signature is created using a private key and can be verified using the corresponding public key, assuring the recipient of the message's authenticity and integrity.
-
Message Authentication Codes (MACs): MACs provide data integrity and authentication. They are similar to digital signatures but are generally faster and require less computational resources. HMAC (Hash-based Message Authentication Code) is a common example.
-
Public Key Infrastructure (PKI): PKI manages and distributes digital certificates, which bind public keys to identities. This is crucial for secure online transactions and communication.
Conclusion: The Ongoing Evolution of Cryptography
While "C 5 9 F 32" itself remains an enigma without further context, its examination provides a valuable opportunity to understand the fundamental principles of cryptography. The security of data relies not only on sophisticated algorithms but also on proper key management, robust protocols, and a continuous awareness of evolving threats. As technology advances, so too must cryptographic methods, constantly adapting to counter new attacks and ensure the confidentiality and integrity of sensitive information. The quest to decode cryptic sequences like "C 5 9 F 32" highlights the ongoing arms race between codebreakers and cryptographers, a dynamic interplay that underpins the secure communication essential for our increasingly digital world. Further investigation would require more data, potentially revealing the underlying cipher, key, or algorithm used to generate this seemingly random string.
Latest Posts
Latest Posts
-
Eukaryotes Vs Prokaryotes Venn Diagram
Sep 23, 2025
-
Ronda Owns A Food Truck
Sep 23, 2025
-
X 2 3x 18 0
Sep 23, 2025
-
Mass Correlation To Kinetic Energy
Sep 23, 2025
-
The 6 X 6 Rule Means That
Sep 23, 2025
Related Post
Thank you for visiting our website which covers about C 5 9 F 32 . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.